On 15 November 2019, I received a VirusTotal notification for a copy of PlugX that had been uploaded ( Yara - PlugXBootLDRCode from https://github.com/citizenlab/malware-signatures/blob/master/malware-families/plugx.yara ).
1 | MD5 : ce67994a4ee7cf90645e93aec084230d |
What stood out from the notification (outside of the file being named plugx.dll) was a compilation time of Fri Oct 4 08:34:45 2019 UTC (a little more then a month before the writing of this post).
Initial Validation
This specific rule matches on operations for assembling a set of API calls - shown below
1 | $ yara -s All.yara sample |
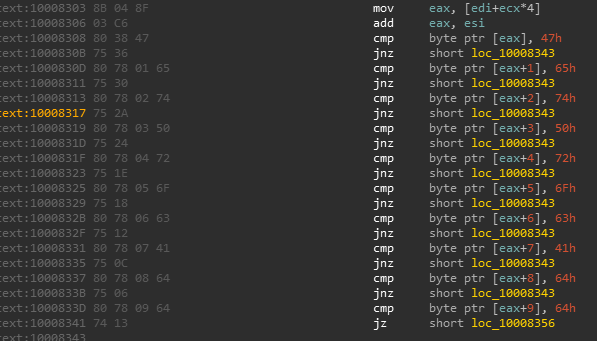
As a general note, the -s flag in Yara is used for outputting the matched strings and is extremely useful for debugging rules and evaluating why a file matched.
From a quick comparison of the strings, a quick Google search found previous reporting confirming this file was PlugX (ref: http://takahiroharuyama.github.io/blog/2014/03/27/id-slash-idapython-scripts-extracting-plugx-configs/)
1 | DEMO... |
Overlaps with versions
A outstanding point of reference evaluating PlugX is the Sophos report (https://www.sophos.com/en-us/medialibrary/pdfs/technical%20papers/plugx-thenextgeneration.pdf). On Page 7, Gabor Szappanos has a table covering the supported commands. In this copy, sub_10008DE acts as a command handler for evaluating operator commands and can be used to evaluate this copy against that from 2014:
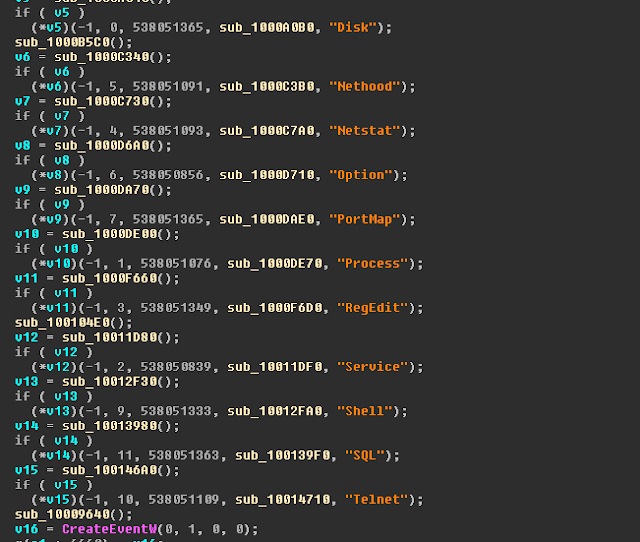
In the above screenshot, many of the commands from the 2014 version are present; some additional commands are present, however, handled withing sub-functions of sub_10008DE.
What did appear unique was a set of commands for monitor clipboard activity:
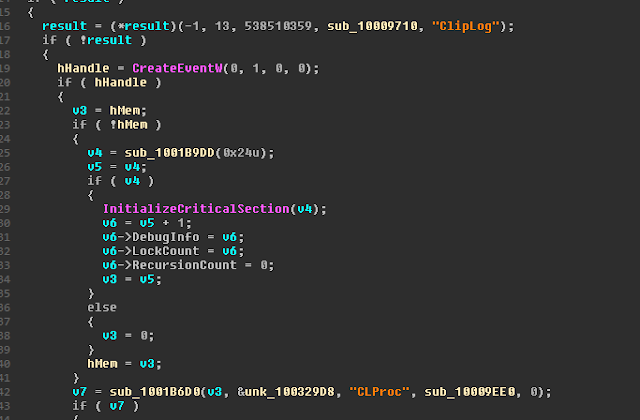
An initial Google search did not show any hits for these being previously documented commands in PlugX - suggesting it may be a new feature - however, further analysis is needed to validate this.